Shallot Routing: An Anonymous Peer-to-Peer Routing Protocol
The Problem with Traditional Anonymity Systems
In today’s digital age, privacy and anonymity are paramount. While tools like Tor have paved the way for anonymous communication, they’re not without their vulnerabilities. Tor's reliance on designated entry and exit nodes creates potential points of attack, leaving users susceptible to traffic analysis and identity leaks. Recognizing these limitations, we present Shallot Routing—a novel peer-to-peer protocol designed to deliver truly anonymous, uncensorable communication without relying on centralized entry or exit points.
Existing systems like Tor and I2P offer robust privacy features but come with inherent trade-offs:
- Tor: While effective for browsing, Tor's reliance on designated entry and exit nodes introduces vulnerabilities. Malicious actors monitoring these nodes can perform traffic correlation attacks, deanonymizing users.
- I2P: Although decentralized, I2P's use of unidirectional tunnels still leaves users open to traffic correlation attacks.
These limitations inspired us to design Shallot Routing, a protocol that prioritizes anonymity within the peer-to-peer network by eliminating entry and exit nodes, obfuscating communication paths, and maintaining sender-receiver indistinguishability.
What is Shallot Routing?
Shallot Routing is an asymmetric peer-to-peer onion routing protocol designed for single-message anonymous communication. Its architecture eliminates the need for centralized nodes by enabling the sender to define both forward and return paths, ensuring that neither the sender nor the receiver can be identified within the network. Figure 1 shows the illustration for shallot routing.
Key Features:
- No Entry or Exit Nodes: Removes key bottlenecks and attack surfaces present in traditional anonymity systems.
- Directed Cycles: Messages are routed through a cycle of nodes, with both requests and responses following the same encrypted path.
- Payload Obfuscation: Ensures that all nodes see only encrypted data, preventing them from determining the sender, receiver, or their own position in the cycle.
- Minimalist Design: Focuses solely on secure, single-message communication.
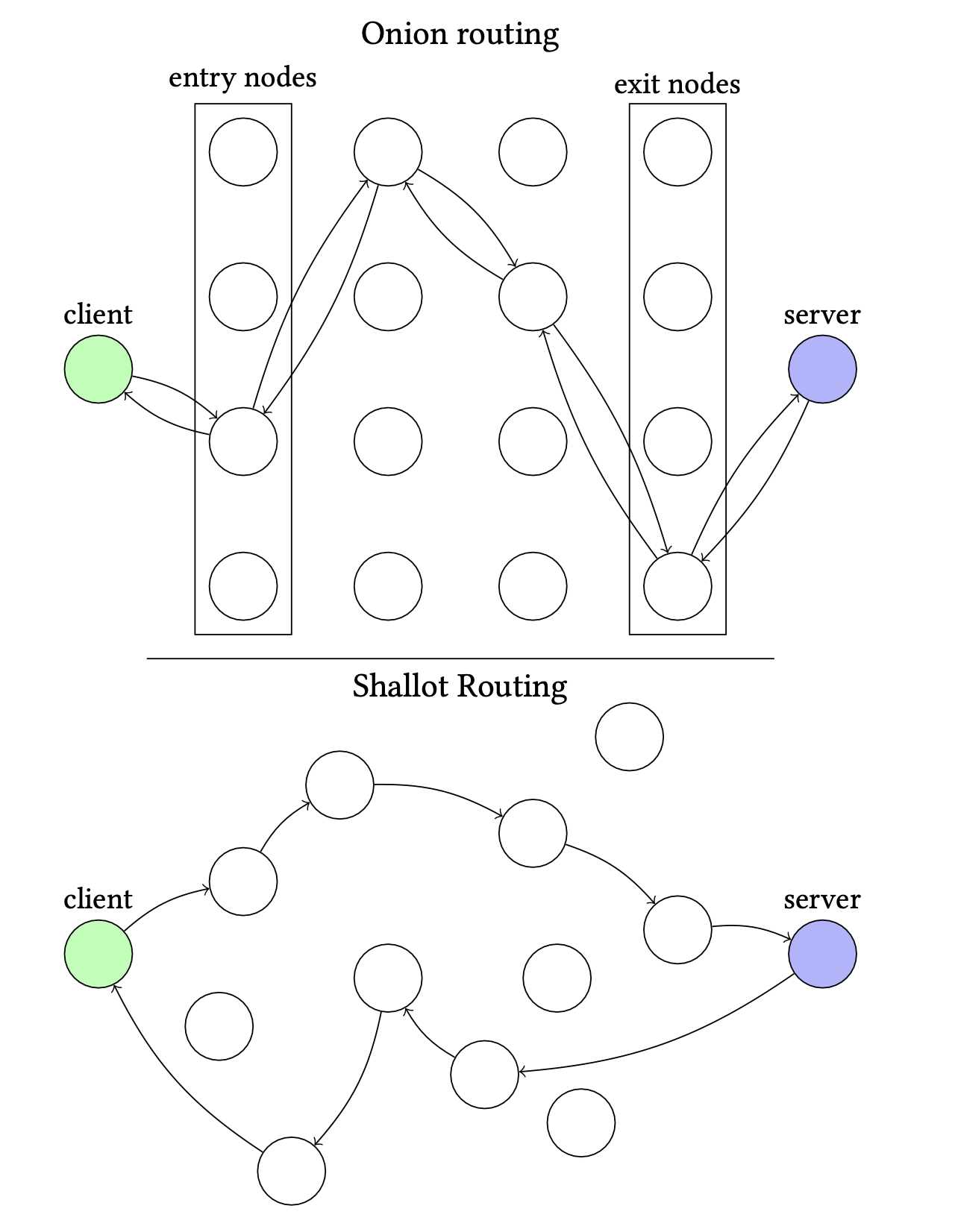
Figure 1: Comparison of Onion Routing and Shallot Routing
How Shallot Routing Works
To understand Shallot routing, let’s consider an example where Alice wants to send a request to Bob. Alice creates a directed cycle of nodes, including herself and Bob, ensuring that at least two intermediate nodes exist between them in both directions. This ensures that no single node can link Alice directly to Bob.
\[ \text{Alice}\to\text{Carol}\to\text{Dan}\to\text{Bob}\to\text{Erin}\to\text{Frank}\to\text{Alice }. \]
Figure 1 illustrates the structure of the Shallot header, which contains routing information encrypted in multiple layers. Each node can only decrypt the information necessary to determine the next recipient, maintaining confidentiality along the route.
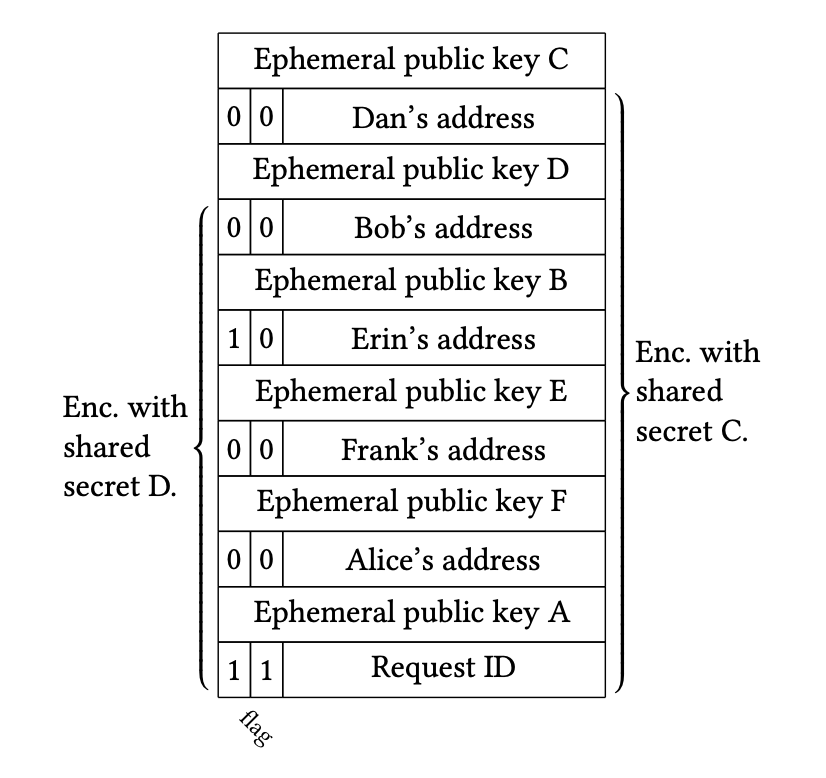
Figure 1: Illustrative structure of the Shallot header
When Alice sends the Shallot header and payload to the first node (Carol), Carol can only decrypt the portion of the header intended for her. Figure 2 shows Carol’s initial view of the Shallot header. After decryption, Carol identifies the next node in the cycle (Dan) and forwards the message as shown in Figure 3.
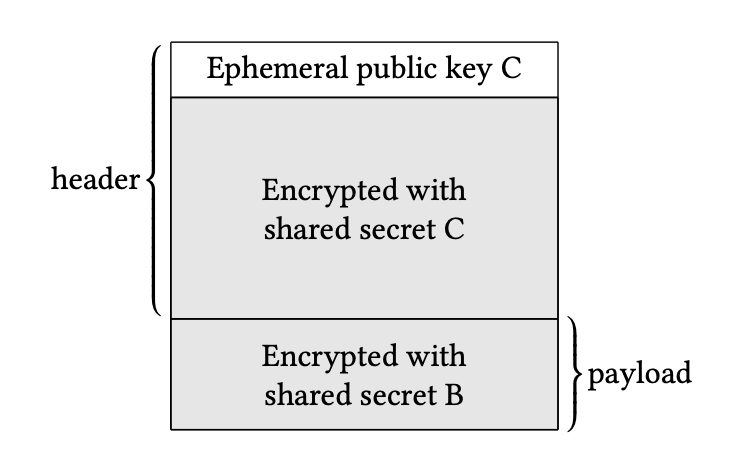
Figure 2: Initial view of the Shallot header as seen by Carol
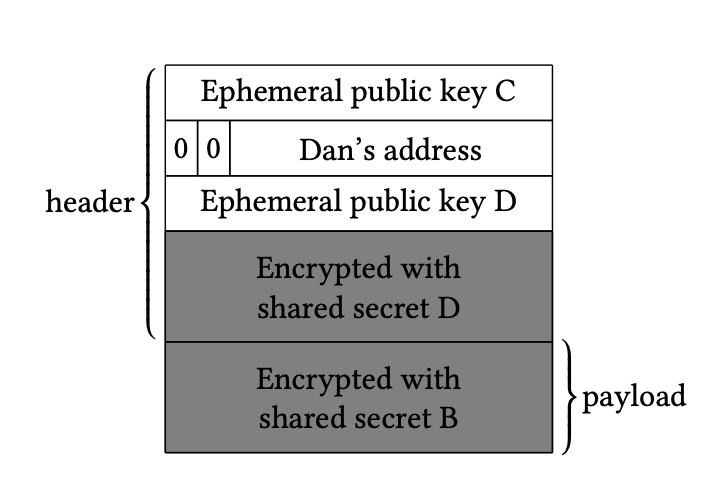
Figure 3: Decrypted Shallot header as seen by Carol after processing
Each node adds random bits to the header before forwarding the message, maintaining the header's original length and ensuring no node can determine its position in the cycle. Figure 4 shows the Shallot header as seen by Dan, who decrypts only the part relevant to him.
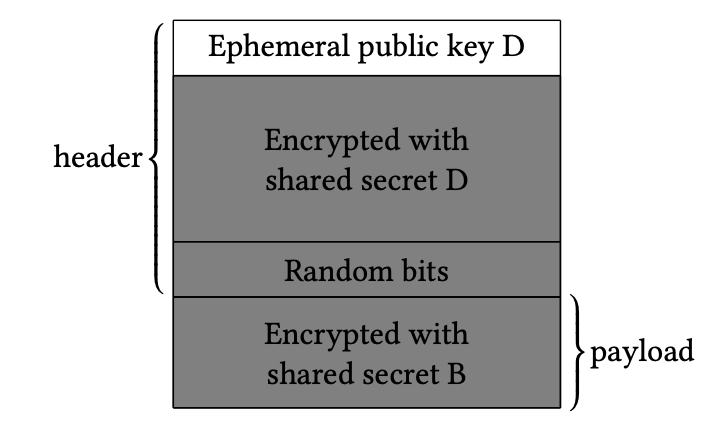
Figure 4: The Shallot header as seen by Dan after receiving the message
When Bob receives the message, he identifies the READ flag in the header, indicating that he should decrypt the payload. Figure 5 shows the Shallot header as seen by Bob after decryption. Bob processes the request, generates a response, and encrypts it to maintain confidentiality along the return path.
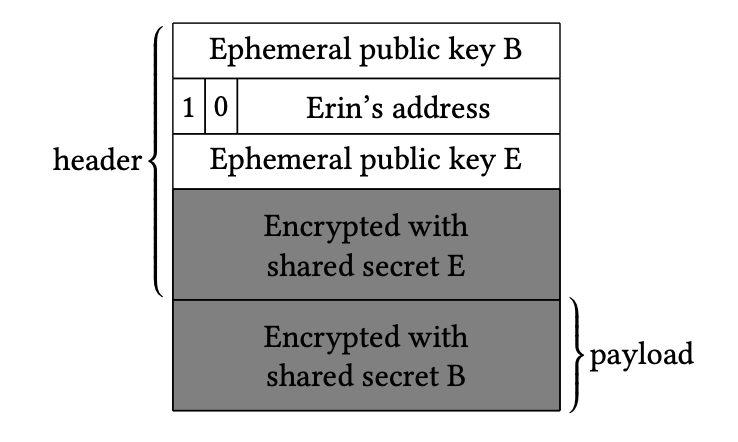
Figure 5: The Shallot header as seen by Bob after decryption
Limitations of Shallot Routing
While Shallot Routing provides robust privacy and anonymity, it is not without its limitations. One notable challenge is its vulnerability to an omniscient adversary who can monitor all network traffic. Although Shallot employs techniques such as consistent payload sizes and randomized node selection to obscure patterns, these measures only provide plausible deniability rather than absolute protection against sophisticated traffic correlation attacks.
Another limitation lies in the dependency on the cycle generation process. The protocol's security and performance rely on constructing cycles with a sufficient number of diverse nodes, but this becomes more difficult as the network scales or when many nodes are offline. Additionally, Shallot’s design requires uniform payload sizes to resist traffic analysis, which can lead to increased bandwidth overhead and latency when dealing with large or irregular data sizes.
Scalability is another area where Shallot faces challenges. While it performs well in smaller, controlled environments, the quadratic increase in latency with longer cycles may limit its feasibility for real-time applications. The protocol’s reliance on a centralized list server also introduces a potential point of weakness, as its compromise could expose metadata about active nodes. Addressing these challenges will be key to enhancing Shallot’s applicability for larger and more diverse networks.
Conclusion
Shallot Routing represents a significant step forward in anonymous communication. By eliminating centralized entry and exit nodes, leveraging directed cycles, and obfuscating message headers, Shallot offers unparalleled privacy for peer-to-peer networks. Its minimalist design ensures efficiency and scalability, making it an ideal solution for applications where anonymity is paramount.
To learn more or contribute to Shallot Routing, visit the GitHub repository.